[vc_row][vc_column][heading animation=”fadeInLeft” animation_iteration=”1″ align=”aligncenter”]Have Hackers Breached Email & Sites You Visit?[/heading][vc_column_text]By Susan Stern. Omaha, NEBRASKA — If you’re security conscious, which everybody SHOULD BE in today’s cyber-hacking era, it’s important to take a variety of steps to protect your PC, email, phone, social media platforms and website.
In this article, I will offer tips on how to protect all of the above, and show you how to check to see if your online accounts may have been compromised. Please note, that I have no personal/professional affiliation with any of these anti-malware detection companies – of the software herein that I may recommend. Also note, that there is no 100% way to be hack-proof.
The hacking of websites, PCs, emails and other online databases where you have entered private information is a common problem. Targets in recent news headlines include Yahoo’s email database, linkedin, Home Depot and Ebay – to name a few.
Before we begin, check to see if your email appears in an international database as being a potential target of hackers. Go to haveibeenpawned.com, a free and safe resource that lets anyone quickly find out if your email address and password may be at risk of being compromised in a data breach.
My results are troubling. Hackers reportedly had access to my email address, passwords, birth date, potentially my full credit card number on the following platforms – leaving me vulnerable to identity theft. Not so fast! Fortunately, I do not use my real date of birth at any online websites, I type personal info utilizing anti-keylogger encryption software online, plus when I enter credit card credentials, I make sure the URL states https, while setting different passwords for all my accounts – tips for all!
[/vc_column_text][vc_single_image image=”8094″ img_size=”full”][/vc_column][/vc_row][vc_row][vc_column width=”1/2″][vc_column_text]In addition, my private login credentials were shared, i.e., “pasted” to a hacker website, as well – potentially for sale in the wild, wild west of the internet – the dark side where crime runs rampant.
[/vc_column_text][heading animation_iteration=”1″ type=”2″ bottom_margin=”nomarb” align=”aligncenter”]Hackers Breached My Email Credentials, Social Sites Plus…[/heading][vc_column_text]* Adobe usernames & passwords
* Gmail username & passwords
* Linkedin email username & passwords
* Malwarebytes email username & passwords
* Myspace (old account) email username & passwords
* Tumblr email username & passwords
[/vc_column_text][heading animation=”bounceInLeft” animation_iteration=”1″ type=”2″ bottom_margin=”lessmar2″ align=”alignleft”]What To Do Right Away If Pawned?[/heading][vc_column_text]If you were pawned, immediately go to all of the above websites that haveibeenpawned.com lists as breached and change passwords. Use a mix of capital letters, lowercase, symbols and characters. Passwords should be longer than 12 characters. If you forgot your password, ask for a reset.
You should use a paid password manager OR, my preference because it is free, maintain a MsWord document which lists all your passwords. If you keep a password list in MsWord, I recommend the purchase of premium Zemana anti-keylogger for this purpose, at $29.95 per year or less if you purchase two or three years upfront. This software is for overall PC prevention from keyloggers that capture and send to the hacker everything you type onto your computer – everything. Make sure you go to the official zemana.com website or visit a trustworthy, reliable third party like cnet.com. Another tip, never re-use the same password for multiple accounts.
[/vc_column_text][heading animation_iteration=”1″ type=”3″ bottom_margin=”lessmar2″ align=”alignleft”]How to Create Strong Passwords [/heading][vc_column_text]* Password should contain 12 -14 characters, minimum, but a longer password is better
* Password should contain a mix of numbers, symbols, capital letters, and lower-case letters
* Don’t use a word that appears in a dictionary
* Don’t depend on substitutions like Ph0enix – isn’t strong because you replaced an o with an 0 (#)
To reiterate, what to do if you have been pawned after using the haveibeenpawned tool? Immediately. Please change your passwords on anything that the free source lists. Now with Yahoo in the news recently for a major email database breach, you’ll want to login there to change your password, if you ever in your lifetime had a yahoo email.
[/vc_column_text][/vc_column][vc_column width=”1/2″][vc_single_image image=”8097″ img_size=”large” alignment=”center”][heading animation_iteration=”1″ type=”4″ bottom_margin=”lessmar2″ align=”aligncenter”]Ever Have Yahoo Email Account? [/heading][vc_single_image image=”8099″ img_size=”full” alignment=”center”][vc_column_text]Keep in mind, if you previously had a Yahoo account, but no longer use it, and the yahoo email remains active, immediately, due to the recently announced 2016 Yahoo email breach, log in and alter your password. Do a password reset if you forgot it, or delete the account permanently.
I personally never liked yahoo email. Years ago, within the marketer & IT communities, those keen to the trends happening, like myself, discussed how security was a major concern. So I ditched yahoo and switched to gmail about eight years ago. Now, I never looked back! Google products are the best.
[/vc_column_text][vc_separator][vc_column_text]Scam Alert. Tighten your Facebook privacy settings, to hide your friend’s list to “only me,” and if a person is already your friend and sends you another friend request – don’t accept it! It could be a fraudster. Contact that friend directly via phone, email or text to see if the friend request is legit. Con artists are stealing people’s Facebook cover pages and profile pics since both the cover/profile images are public. 
If your page is cloned, and your friend’s list is public, they’ll send friend requests in your name to your social circles, and then send them messages about “claiming a prize”. This is an attempt to steal money, and may lead to identity theft. Facebook doesn’t allow you to hide your cover page or profile image – something the social media platform should do – to prevent these phishing scams. Scammers have duplicated official church Facebook pages, and then asked for donations. If you are victimized, report fake account to Facebook right away.
[/vc_column_text][/vc_column][/vc_row][vc_row][vc_column][vc_custom_heading text=”What Anti-Virus Does My PC Need?” font_container=”tag:h2|text_align:center” google_fonts=”font_family:Cabin%3Aregular%2Citalic%2C500%2C500italic%2C600%2C600italic%2C700%2C700italic|font_style:400%20regular%3A400%3Anormal”][box_text animation_iteration=”1″ icon=”fa-lock”]Without a doubt, every computer should have anti-virus software, a firewall (comes bundled with anti-virus software), an extra anti-malware application called malwarebytes (despite previous breach displayed in haveIbeenpawned), and an anti-keylogger program. Don’t forget to set a strong password on the wireless router (options to set two passwords on mine) and don’t leave it open for goodness sake. Also, don’t label it with your name or other identifying information including the manufacturer.
I am also exploring the purchase of a VPN. As howtogeek.com defines it, “a VPN, or Virtual Private Network, allows you to create a secure connection to another network over the Internet. VPNs can be used to access region-restricted websites, shield your browsing activity from prying eyes on public Wi-Fi, from the local network and your internet service provider.” It’s an extra layer of security.
[/box_text][vc_column_text]
[/vc_column_text][/vc_column][/vc_row][vc_row][vc_column][call_to_action animation_iteration=”1″ style=”2″ icon=”fa-bookmark” title=”Specific Software Suggestions”][vc_column_text css=”.vc_custom_1475374687140{background-position: 0 0 !important;background-repeat: no-repeat !important;}”]
** McAfee premium. Run scan every day, at least once per week (it may be free with ISP) Panda, Kaspersky, Norton, Avast appear to be quality anti-virus programs, too.
** Zemana antilogger premium, $29.95 per year. Changes to gibberish keys you type online & on PC, including Microsoft products like MSWord, Excel. Free trial available
** Malwarebytes free version. Run program every week, or every day
** Coxtechsolutions premium PC support 24/7, about $14.99 per month for 3 computers. CALL your ISP for more info
[/vc_column_text][/vc_column][/vc_row][vc_row][/vc_row][vc_row][vc_column width=”1/2″][vc_custom_heading text=”Do You Need Smartphone Anti-Virus?” font_container=”tag:h2|text_align:center” google_fonts=”font_family:Cabin%3Aregular%2Citalic%2C500%2C500italic%2C600%2C600italic%2C700%2C700italic|font_style:400%20regular%3A400%3Anormal”][vc_column_text]My apologies IOS users. In this article today, we’re focusing primarily on Android devices – PCs – not Macs. Anyhow, your smartphone is a mini computer, so you should install several software apps to protect your sensitive data. You should encrypt your phone, go to settings, and set up a password. If someone were to steal your phone, they have access to all your info: images, email account, social media sites and more. Again, nothing is 100% hack-proof. Here’s what I suggest to install on an Android phone, found at the Google Playstore:
** Avast anti virus free & cleanup
** Zemana Safe Keyboard free
** Malwarebytes free
** Wifi Inspector free. See if someone is connected without your permission
** Mr. Number. Install a free call blocker like Mr. Number for Android & IOS devices. It blocks many known scammer calls/texts, prevents private & unknown calls, and gives you details about them. Should a scammer or annoying telemarketer get through, you can block the number for the future, then tell fellow members who/what they are, or spoofed number they use.
The bad news is that there does not appear to be, at the date of publication, reliable anti-wiretapping or wire tapping phone detection programs on the market. This is kinda scary especially if you spearhead a controversial PR or election campaign.
On September 27, 2016, CNN reported the FBI is investigating a small number of Democratic staffer’s cell phones that were potentially hacked during the ongoing presidential race.
Hacking cell phones has become a real issue, with detection reportedly difficult. Reports indicate that hackers have the capability to receive a recording of every phone call you make, turn on the mike/listen anytime, read your texts, receive all images, and so on – just like hackers can/do remotely turn on a desktop or laptop camera. Of course, for your laptop or desktop, a gold rule of thumb is to place tape over your webcam lens, as FBI Director James Comey recently admitted to doing in an offhand Q&A session at Kenyon College covering the topics of encryption and privacy, reports NPR.
My research also shows that not all hackers have to physically have possession of your smartphone to add a keylogger.
On a security forum at Quora.com, it’s reported that “phone users have reported strange SMS text messages received as an initial attempt to hack a smartphone. Texts that appear as a single square or other strange characters are attempts by hackers to download spyware or malware onto your device. These attacks are similar to malicious email viruses, however on a mobile device the SMS only has to be received by the smartphone, with no download action taken by the user.”
If you suspect something is not right. You are encouraged to examine your cellphone bill for unauthorized charges and calls, ascertain if the battery is draining extremely fast, and if your phone sends texts by itself, opening and closing apps, and exhibiting other cray-cray behaviors.
Prevention is helpful. Tech experts suggest you update your phone’s firmware to the most current version. Set a password on the phone. Avoid leaving the phone alone in a public place like a restaurant or at the office. Protect the phone with anti-virus, anti-malware and anti-logger apps. Don’t do any shopping or banking on a public WiFi network. If you’re still concerned, then Google instructions how to do a “factory reset.”
[/vc_column_text][/vc_column][vc_column width=”1/2″][vc_single_image image=”8137″ img_size=”large”][vc_single_image image=”7507″ img_size=”large”][vc_single_image image=”7047″ img_size=”full”][/vc_column][/vc_row][vc_row][vc_column][box_text animation_iteration=”1″ icon=”fa-key” title=”Extra Website Security Key”]Hackers are hitting websites every day, not just the big guys like governmental agencies, institutions and huge corporations. No website is immune including small business. All website content systems are vulnerable.
Here in Omaha, industry fellows I know all report that client websites have been targeted by hackers including their own, demonstrating the need for 24/7 website monitoring services, removal, and database backups. Again nothing is 100% hack-proof, completely hack-resistant.
As a marketer/PR practitioner, who manages client websites and content, I strongly, without a doubt, recommend purchasing a third party service like sucuri.net for daily website monitoring, malware removal, cloud proxy firewall and database backup. Again, I am not a reseller, and receive zero residuals from any of my recommendations herein.
Another tip. Make sure you have your marketer/PR practitioner update any website plugins, and the CMS, website content management system, too – monthly.
Again. You’ll want to make sure your website is backed up, so you can rely upon it, if the website breaks during the CMS (content management system, like WordPress or Joomla) updates.
Remember. Even with these extra preventative measures, your website is still vulnerable to a hack attack. Don’t blame your marketer! LOL. That said, the nice thing about sucuri.net, you can blacklist countries most identified as hackers: Russia, China and India. You’ll receive 24-hour support if your site gets hit. It costs a mere couple hundred per year for this service. I have it, and all my clients do, as well.
[/box_text][/vc_column][/vc_row][vc_row][vc_column width=”1/2″][heading animation=”swing” animation_iteration=”1″ type=”2″ align=”aligncenter”]Email Security Essential! Holds Secrets Must Protect[/heading][/vc_column][vc_column width=”1/2″][heading animation=”swing” animation_iteration=”1″ type=”2″ align=”aligncenter”]Education: Password Security Videos![/heading][/vc_column][/vc_row][vc_row][vc_column width=”1/2″][vc_column_text]Consider changing your password every few months as a precaution, using over 12-14 characters, with a mix of capital & lowercase letters, symbols and #s, as above outlined. Don’t open emails from someone you don’t recognize – delete it. A hacker can send you an email with a hidden .exe file, which can instantly install a keylogger on your computer that your anti-virus, anti-malware and anti-keylogger programs do not, cannot, may never detect.
FYI. Under many instances, you wouldn’t even know if a keylogger is secretly installed on your PC. A keylogger may be installed remotely via email attachment (software) or by manually installing it to your computer (hardware).
While there are legit uses of keyloggers, say to monitor employees or for parents keeping eyes on a child’s online behavior (although, I personally believe both these instances are violations of privacy, and not cool unless a suspicion of malfeasance exists), keyloggers are often used illegally for nefarious reasons by business competitors, from opponents in PR & election campaigns, an ex husband or former friend, and other bad folk with the goal of stealing personal communications, pictures, emails, bank account info, company secrets and more.
From my understanding, authorities won’t pursue small stalking via keylogger cases especially domestic kinds, but will pursue those involving felony crimes or substantial financial fraud suspected.
Lack of resources is one reason.
Beware. A keylogger can be a major problem for you.
[/vc_column_text][heading animation=”fadeIn” animation_iteration=”1″ type=”2″ bottom_margin=”lessmar2″ align=”aligncenter”]Signs Your PC May Be Hit By Keylogger![/heading][vc_column_text]** PC freezes a lot
** PC shuts down and starts up by itself
** Cursor moves
** Someone you know shares information with you, only you would know based on your computer activity
Fact is. Every day, hackers try different ways to attack computers. They are stealth. Not all the anti spyware programs are up-to-date and able to catch the latest Trojans, worms and malware. So, as a matter of practice, at least once a week, scan your computer.
That said, remember not all anti-spyware, anti-malware and anti-keylogger programs detect the intrusions. So, if you are suspicious of a breach like your computer is freezing up often and the free CCleaner registry fix does not resolve the problem, I might consider running additional malware detection & removal tools like Spydotsearchanddestroy (free), SUPERAntiSpyware (free & premium versions available).
Behind Zemana.com premium, my second choice, with few anti-keylogger options available, is Spyshelter premium. Take note, even a computer savvy person like myself found that Spyshelter’s dashboard/settings confuse. Be careful. You might end up wrecking your PC by removing something essential. I don’t like this program – the dashboard is difficult to understand.
[/vc_column_text][/vc_column][vc_column width=”1/2″][vc_column_text]
[/vc_column_text][vc_column_text]Google’s “HTTPS Everywhere” campaign is underway, attempting to force every website and blog to switch to secured encryption by January 2017. You’ll get a slight ranking boost, when you do so. Google Chrome Browser meantime soon plans to mark in red as “UNSAFE” websites that fail to make the switch from HTTP to HTTPS.
Right now, you can spot in your browser a gradual shaming of un-encrypted websites – they are marked with an “i” in the address bar. Call your marketer to schedule the move. Your website should be put in maintenance mode for the migration expected to take 24-96 hours. 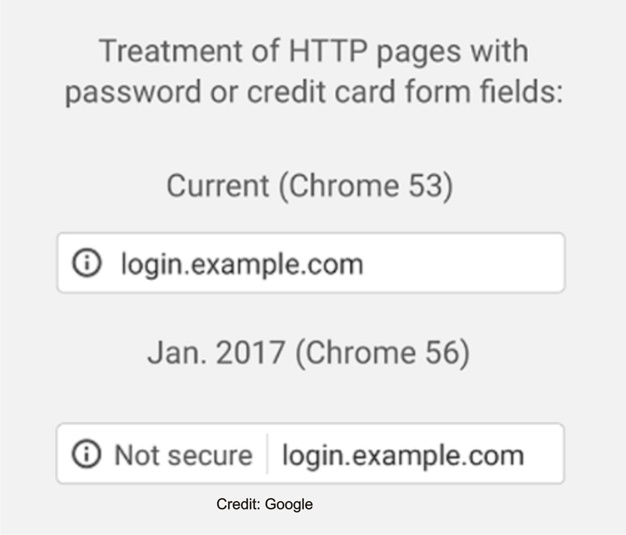
[/vc_column_text][/vc_column][/vc_row][vc_row][vc_column width=”1/2″][section][vc_column_text]
[/vc_column_text][/vc_column][vc_column width=”1/2″][heading animation_iteration=”1″ type=”2″ align=”aligncenter”]How to Spot Email Phishing [/heading][vc_column_text]If you use email, you need to think about security! The experts say you should learn how to spot phishing emails.
The FTC, Federal Trade Commission defines phishing:
“When internet fraudsters impersonate a business to trick you into giving out your personal information, it’s called phishing. Don’t reply to email, text, or pop-up messages that ask for your personal or financial information. Don’t click on links within them either – even if the message seems to be from an organization you trust. It isn’t. Legitimate businesses don’t ask you to send sensitive information through insecure channels.”
[/vc_column_text][/vc_column][/vc_row][vc_row][vc_column][call_to_action animation=”tada” animation_iteration=”1″ style=”2″ icon=”fa-check” title=”The FTC Gives Phishing Examples”][vc_column_text css_animation=”left-to-right”]You open an email or text, and see a message like this:
1) “We suspect an unauthorized transaction on your account. To ensure that your account is not compromised, please click the link below and confirm your identity.”
2) “During our regular verification of accounts, we couldn’t verify your information. Please click here to update and verify your information.”
3) “Our records indicate that your account was overcharged. You must call us within 7 days to receive your refund.”
The senders intend to “phish” for your info – and use it to commit fraud.
[/vc_column_text][call_to_action_3 animation_iteration=”1″ title=”How to Deal with Phishing Scams”][vc_column_text]
1) Delete email & text messages that ask you to confirm or provide personal information (credit card and bank account numbers, Social Security numbers, passwords, etc.). Legitimate companies don’t ask for this information via email or text.
2) The messages may appear to be from organizations you do business with – banks, for example. They might threaten to close your account or take other action if you don’t respond.
3) Don’t reply, and don’t click on links or call phone numbers provided in the message, either. These messages direct you to spoof sites – sites that look real but whose purpose is to steal your information so a scammer can run up bills or commit crimes in your name.
4) Scammers can make it appear on caller id that the number they are calling from is your bank.
5) Local area code calls may not actually be local
6) call your bank or business you make payment to direct, found on statements
[/vc_column_text][box_text animation_iteration=”1″ icon=”fa-lock” title=”Action Steps. according to the FTC, edited”]1) Use trusted security software. Set auto updates
2) Don’t email personal or financial information. Email is not secure method for personal info transmission
3) Only provide personal or financial information through an organization’s official website that you typed yourself. Look for https (the “s” stands for secure) when you share sensitive data. Unfortunately, as the FTC reports no indicator is foolproof; some phishers have forged security icons
4) Review credit card & bank account statements, each month for unauthorized charges
5) Be cautious about opening attachments and downloading files from emails, regardless of who sent them. These files can contain viruses or other malware that can weaken your computer’s security
The Federal Trade Commission asks you to report, by forwarding phishing emails to spam@uce.gov — and to the company, bank, or organization impersonated in the email.
[/box_text][vc_separator][/vc_column][/vc_row][vc_row][vc_column width=”1/2″][heading animation_iteration=”1″ type=”2″ align=”aligncenter”]Beware Ransomeware – Popups Claim PC Virus [/heading][vc_column_text]It’s happened to me. If you browse the internet & open a malicious site, you may receive a pop up screen that your computer has been compromised. Immediately press CTL, Alt & Delete which opens Task Manager. End process of the browser window you were using when the pop up occurred. Many times by exiting the application, the phony “virus” warning disappears – there is no malware. Other times, your PC will get hit with a variation of ransomware that may require a bona fide technical support company to unlock via safe mode.
How this ramsomware tends to work is that, after visiting a suspicious website, a screen overtakes your computer. There is a warning that you have to call the listed phone number, in order to remove the virus. Once you call “certified Microsoft tech support”, the overseas scammer remotely accesses your computer, with your permission, and requires you to pay a fee to “remove the malware”.
The reality is that you have no virus to remove – yet. Instead, the con artist installs a fake program and claims it shows viruses “all over your network.” The fact is the scammer installed a keylogger – to record all your keystrokes to steal your confidential info.
Watch this video to see how these scammers attempt to con.
[/vc_column_text][vc_column_text][/vc_column_text][heading animation_iteration=”1″ type=”2″ align=”aligncenter”]Take Steps to Secure Accounts & Devices[/heading][vc_column_text]Having been the recipient of ransomware. a keylogger target, and with email, website and social media accounts compromised, I want to share with everybody – the importance of taking security – very seriously!
I Shall Repeat. ATTENTION EVERYBODY. It’s crucial & extremely important to use a mix of paid and free security measures on all devices that come from official, reputable companies.
In this day in age of cyber crimes aplenty, do all you can do to protect your PC, email, phone, social media platforms and business website.
Stay safe out there. The cyber world is indeed a scary place. That said. Don’t get overwhelmed and fearful. Simply be vigilant. Stay informed. Take precautions. You will be okay!
[/vc_column_text][/vc_column][vc_column width=”1/2″][vc_single_image image=”8101″ img_size=”large”][vc_single_image image=”8103″ img_size=”full”][vc_single_image image=”6786″ img_size=”full” alignment=”center” onclick=”custom_link” img_link_target=”_blank” link=”https://sternprmarketing.com/contact-omaha-marketing-firm” title=”Security Key On All Devices!”][vc_column_text css_animation=”left-to-right”]Now, of course, if something bad happens, give Stern PR Marketing in Omaha, Nebraska a call or send a note, we will help your business or organization get back on track, give advice and assist you in beefing up security. 🙂
— end —
[/vc_column_text][/vc_column][/vc_row][vc_row][vc_column][call_to_action animation=”tada” animation_iteration=”1″ icon=”icomoon-contact-add” title=”Contact Stern PR Now! ” url=”https://sternprmarketing.com/contact-omaha-marketing-firm”][/vc_column][/vc_row][vc_row][/vc_row][vc_row][/vc_row][vc_row][/vc_row][vc_row][/vc_row][vc_row][/vc_row][vc_row][/vc_row][vc_row][/vc_row][vc_row][/vc_row][vc_row][/vc_row][vc_row][/vc_row]